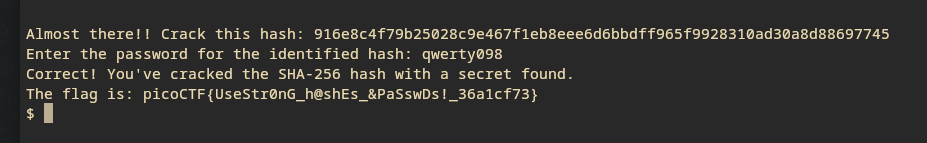
- Problem statement
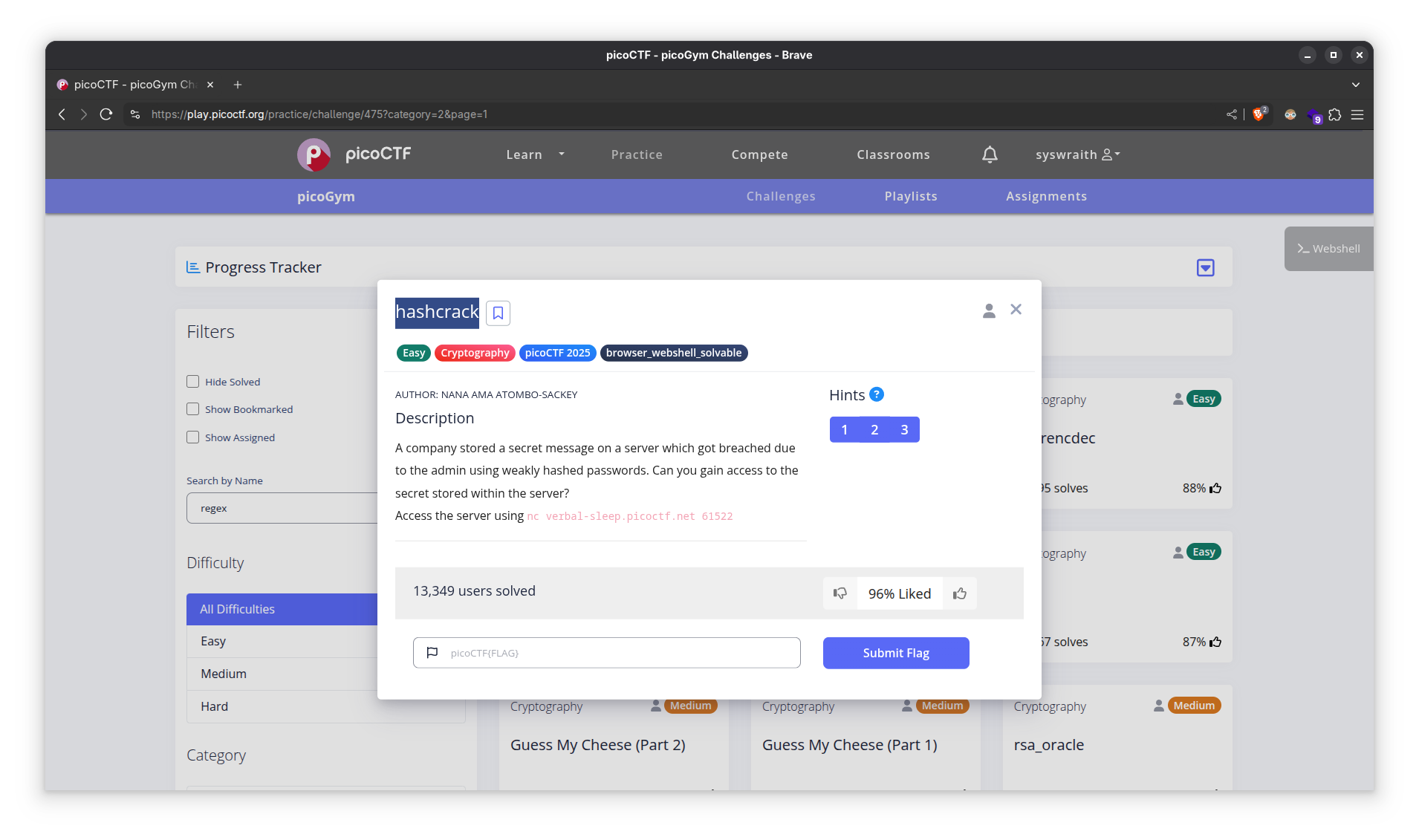
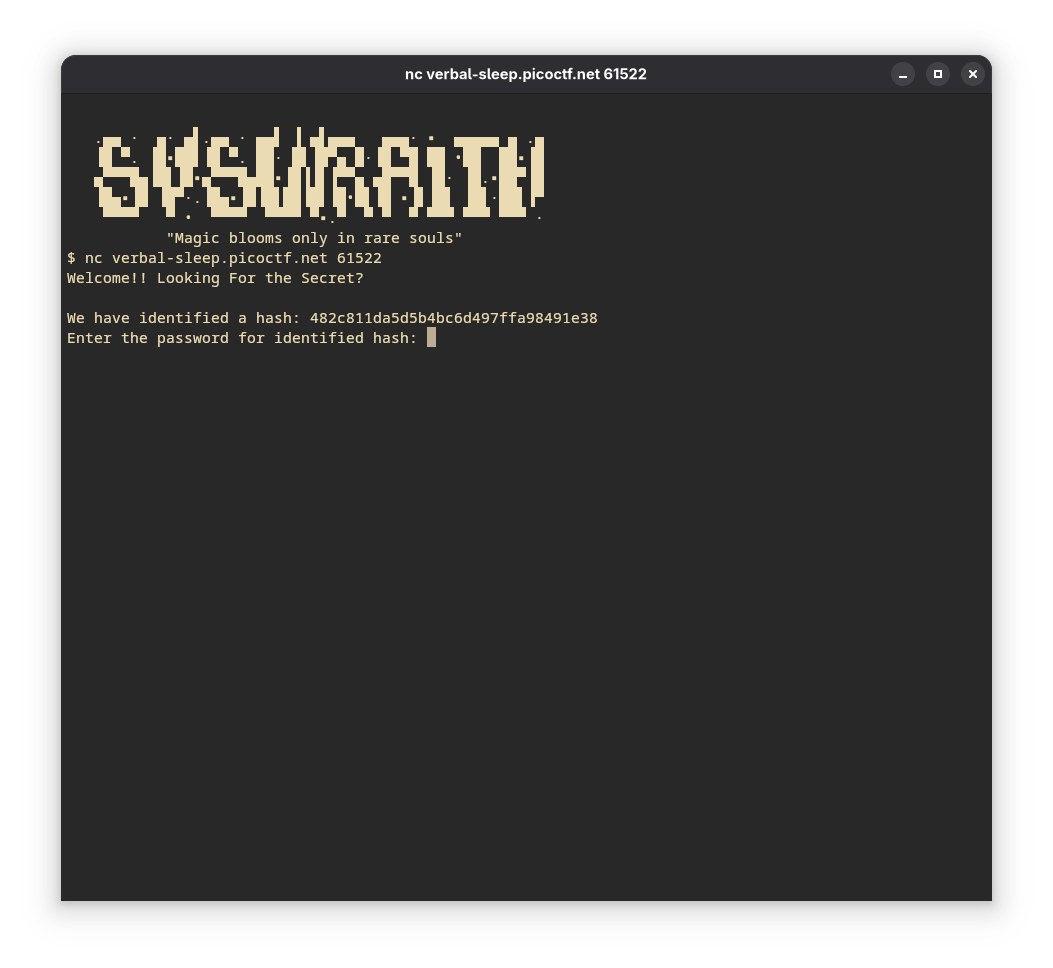
- Install hashcat and rockyou.txt. Save the identified hash in a file (here I’m saving it in the file
company.hash). - There’s a ton of hashing algorithms that
hashcatcan crack. A list of them is available at https://hashcat.net/wiki/doku.php?id=example_hashes - Start the bruteforce attack with the following command. The
--showflag tells us which password matches the given hash.
hashcat -m 0 company.hash rockyou.txt --show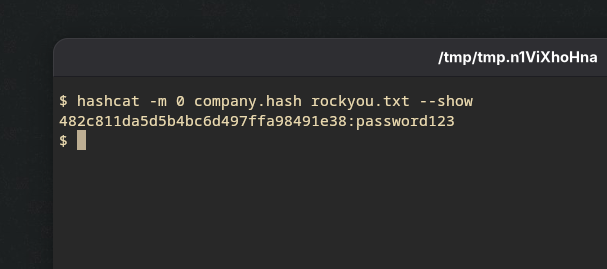
- On entering the hash, another hash is given to us. This should be fun :)
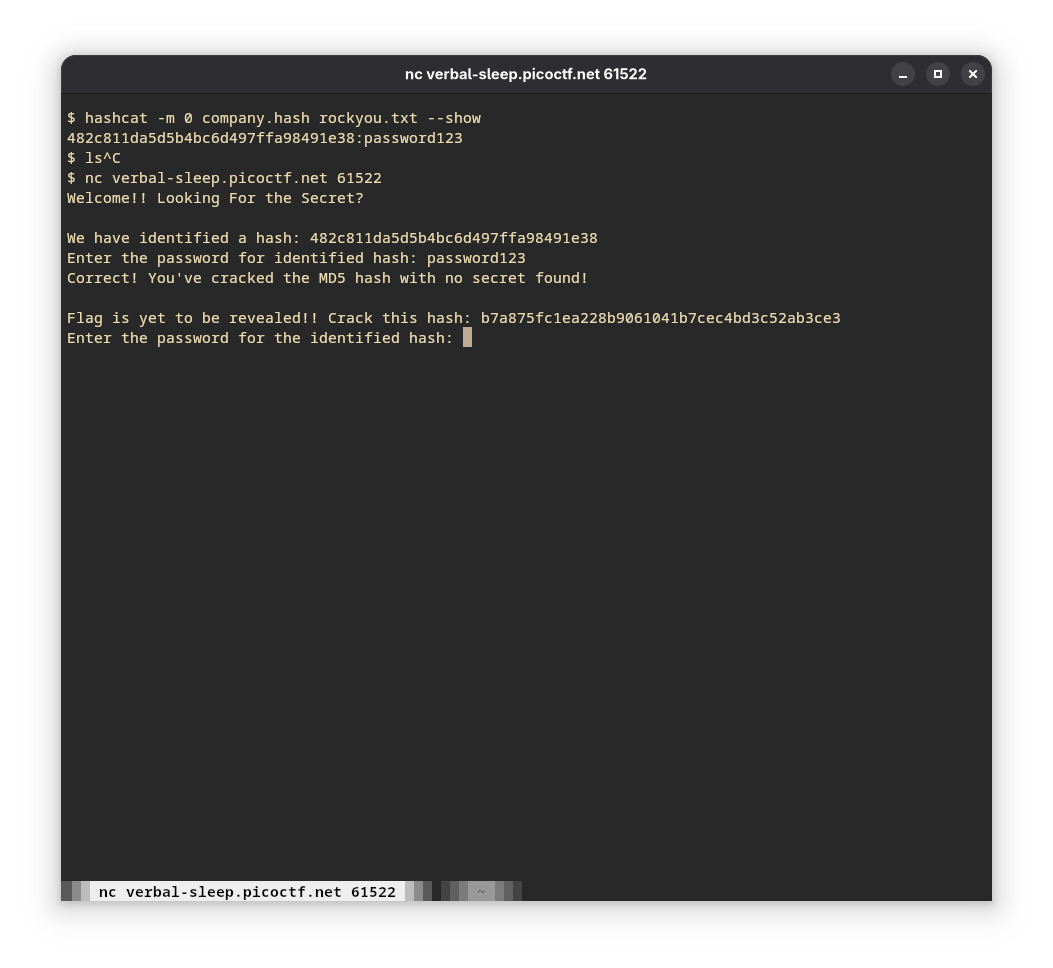
- On trying to break it with MD5, we get the following error.
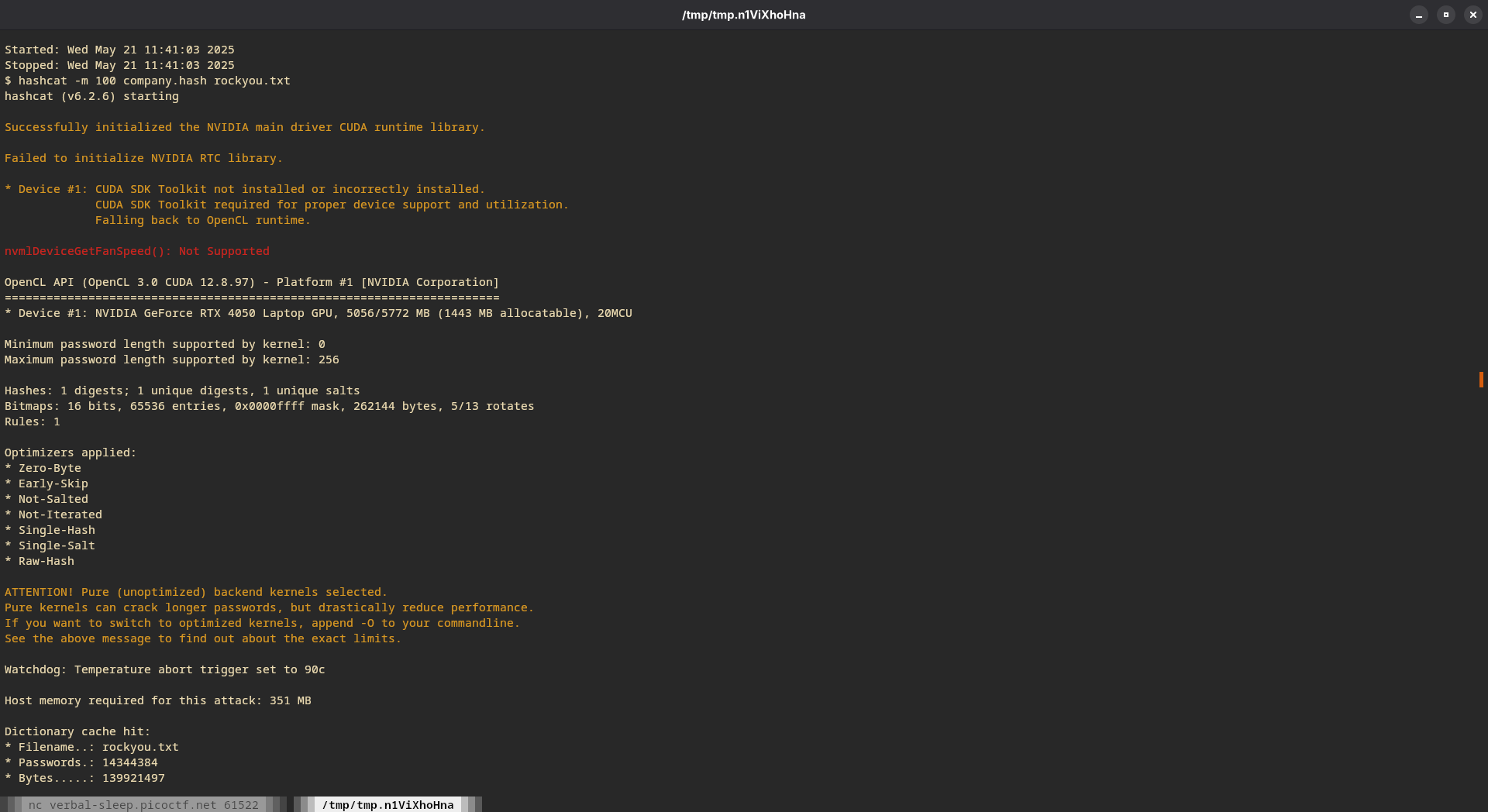
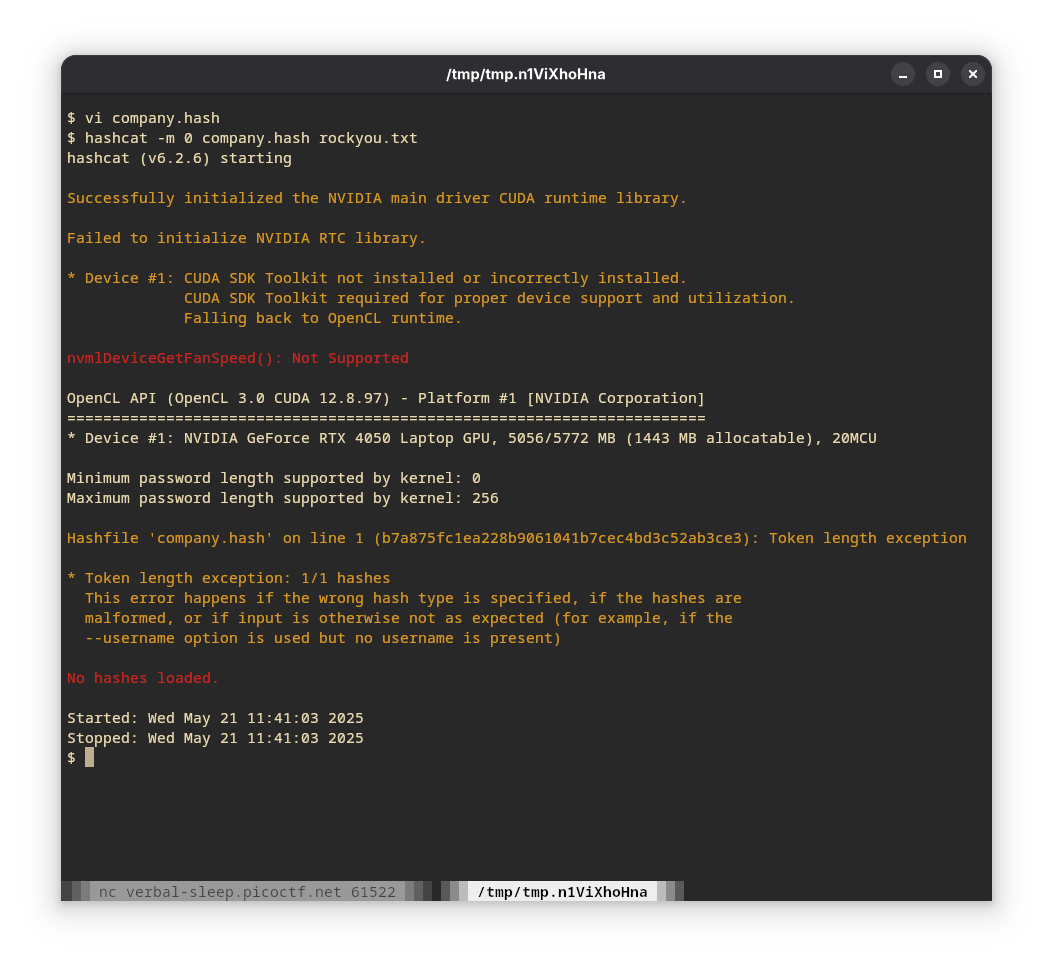 7. Not MD5. Going back to the list mentioned in step 3. Maybe…SHA1? Yes!
7. Not MD5. Going back to the list mentioned in step 3. Maybe…SHA1? Yes!
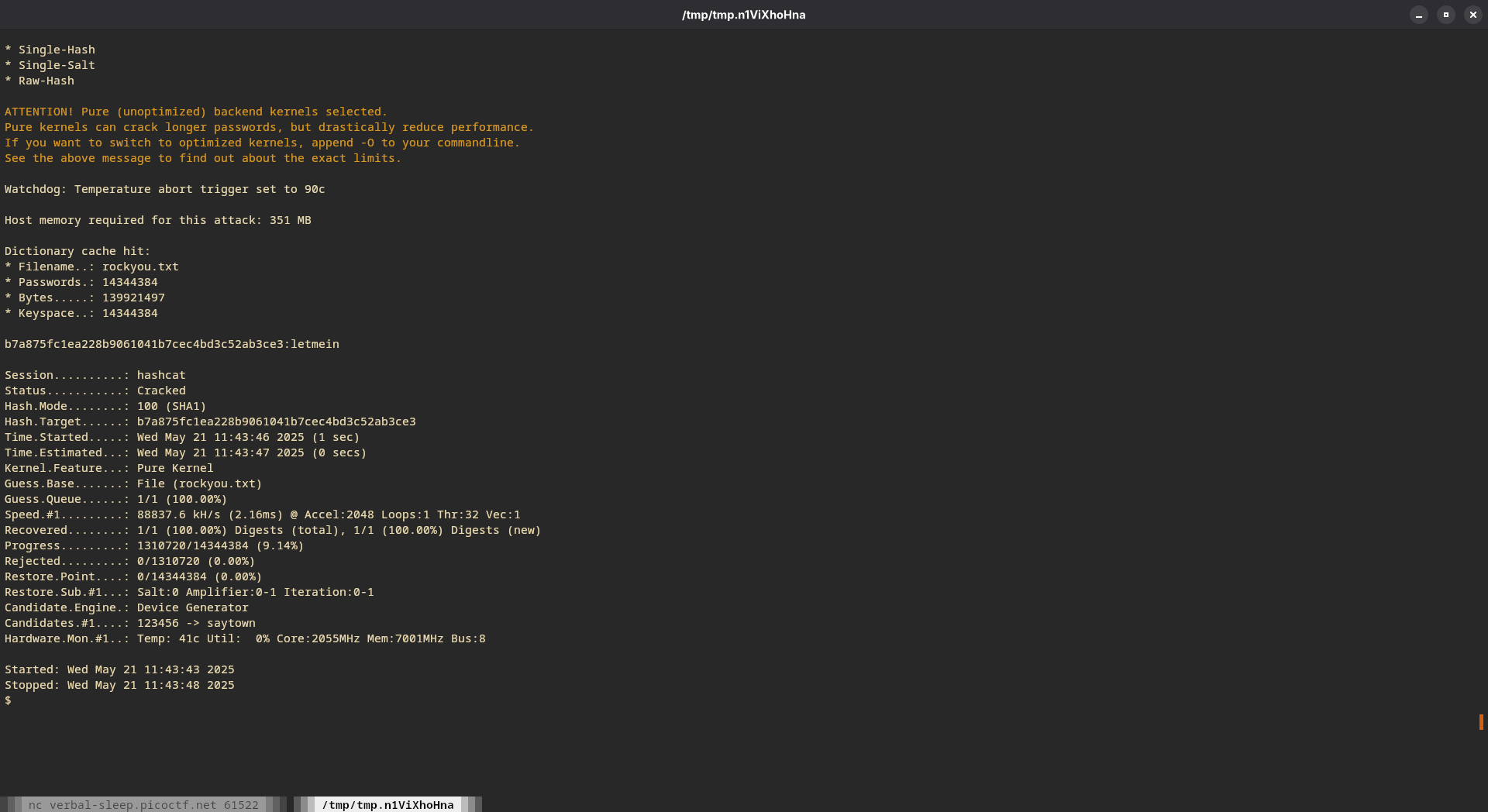
- Another hash!
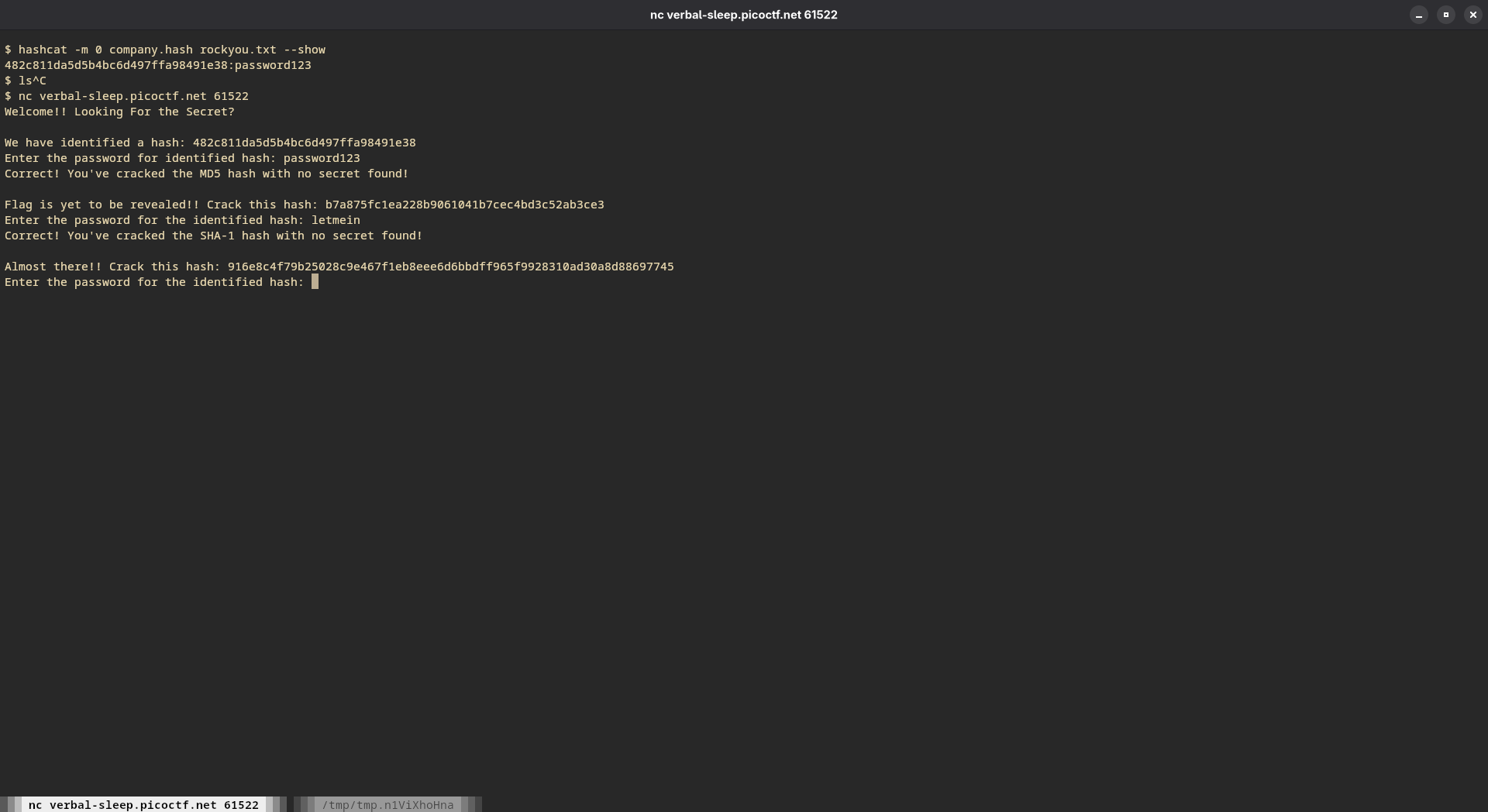

- Counting the number of characters, we can see that it’s 64 characters in length. Which means that we need an algorithm which outputs a 64 character hash. A quick search tells us that
SHA2-256is what we’re looking for.
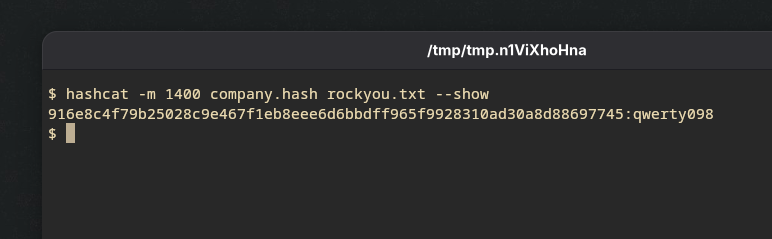
- And there we have it!